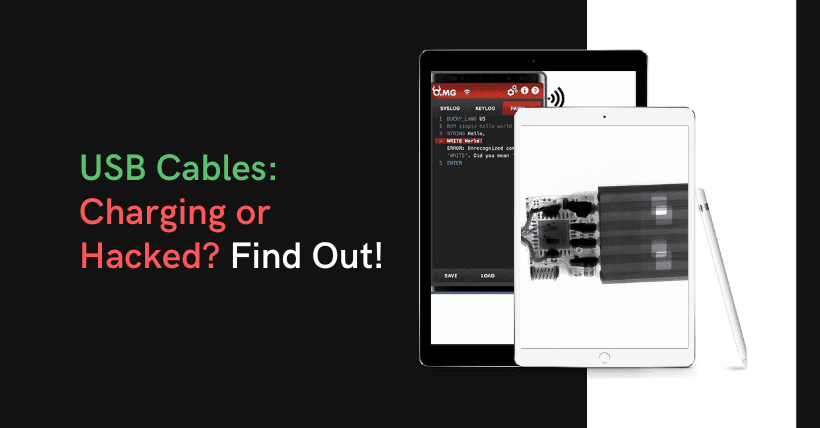
It’s like this, recently when I was browsing the internet, I came across a mind-buzzing dangerous thing:
O.MG Cable

It looks like an ordinary guy of USB connecting wire, but in reality, it’s a computer that carries 200+ malicious software and can even connect to WiFi.”
“Where is the computer?” It’s hidden inside the white plastic circle of the USB-A port.

If anyone treats it as an ordinary USB cable and plugs it into a phone or computer, this seemingly “harmless” connecting cable can immediately transform into an all-powerful hacking tool.

Its main method of disruption is disguising itself as various types of USB devices.
Let’s take the simplest example to understand its capabilities:
The O.MG Cable can pretend to be a USB keyboard. So, when a user plugs it into a computer, besides passing through the data from the phone on the other end of the cable, it will also make the computer recognize it as a new USB keyboard.
On most computers, plugging in a new keyboard doesn’t trigger a new notification. Even if there’s a sound indicating the connection of a USB device, users would simply assume it’s the computer recognizing their phone.
As a keyboard, the O.MG Cable gains the ability to send various commands to the computer directly. For example, it could command the computer to “search the hard drive, find all images on the computer, and then upload them to a designated server.”
Similar scanning and uploading actions wouldn’t alert ordinary security software because they would appear as normal keyboard operations.
At this point, if this computer is connected to the internet, there’s virtually nothing preventing all the photos from your hard drive from appearing on the hacker’s server.
However, even if the victim’s computer isn’t connected to the internet and uploading is not possible, there’s no need to worry.
The microcomputer inside the O.MG Cable comes with a built-in WiFi transmission module!
It can first transfer data from the victim’s computer to its storage device, and then transmit it to the attacker via WiFi.
No network card? No problem, O.MG Cable has you covered.
Now, say: Thank you, O.MG!
What’s even more lethal is that all of the seemingly complex operations mentioned above require minimal technical expertise within the O.MG Cable’s “penetration testing” (plugin marketplace) ecosystem.
Behind the O.MG Cable is an extensive community, comprising numerous actual technical professionals, who share various codes for “penetration testing.”
Here, “payload” refers to the testing code.
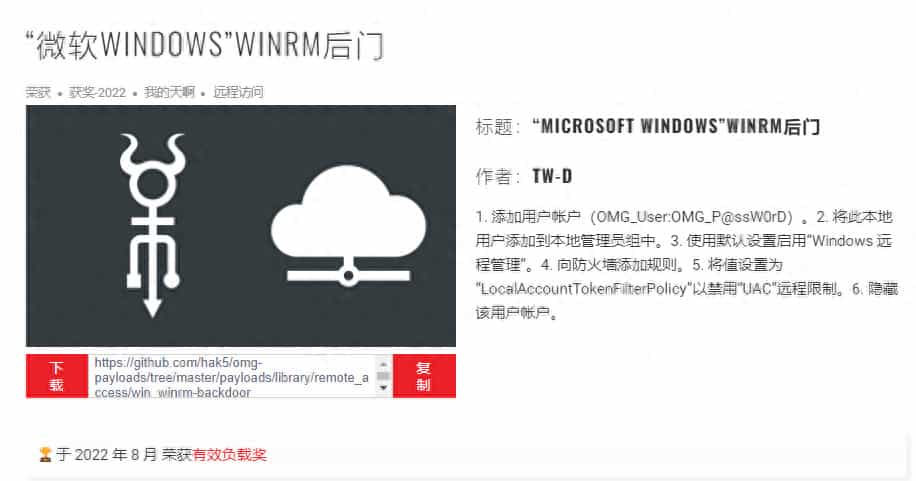
For instance, scripts like this that create backdoors on Windows:
And also this script that steals passwords from Mac computers:

There are even scripts targeting Android devices:
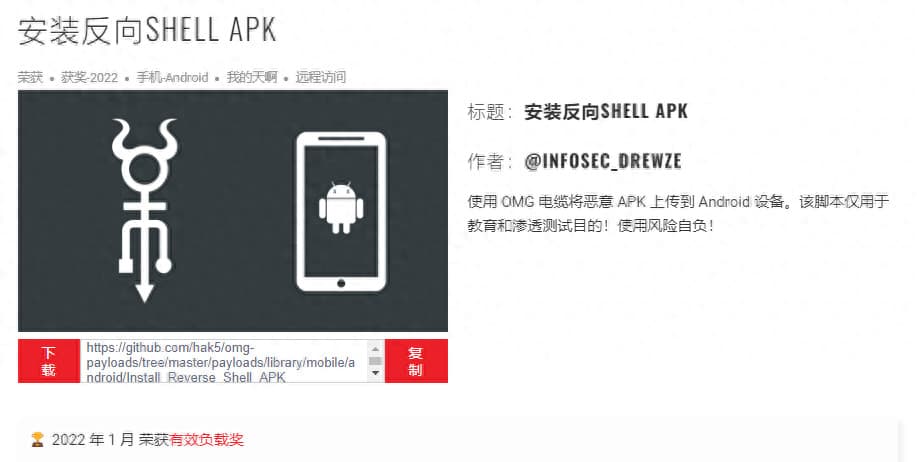
In other words, attackers only need a basic understanding and some Ctrl C/V (copy-paste) skills to execute a complex attack using this cable.
As a hardware editor with a grasp of coding, I’m fully confident that I could spend a week of my free time and, with the assistance of documentation and the community, complete the entire set of attack procedures demonstrated earlier.
The capabilities of the O.MG Cable are truly beyond imagination.
Tony has come across publicly available camouflage hacking tools before, but previous ones either lacked such deceptive appearances, had simpler functionalities, or could only target severely outdated systems with weak security.
Meanwhile, most individuals are completely unaware that even a simple USB cable could conceal secrets.
What we can do at present is to raise awareness:
Never use USB charging ports, cables, or devices of unknown origin.
This is especially critical for individuals with confidentiality or security requirements in their roles.
Related:
- Recover Inaccessible USB Drives: Expert Guide to Revival
- Easy DIY: Add Type-C Port to Regular Charger!
- WiFi 7 Isn’t Here Yet, and WiFi 8 Is Already Coming!

Disclaimer: This account maintains a neutral stance on all original and reposted articles, and the views expressed therein. The articles shared are solely intended for reader learning and exchange. Copyright for articles, images, and other content remains with the original authors. If there is any infringement, please contact us for removal.