In recent years, we used to often see the content ‘supports AES256 encryption’ in solid-state drive introductions, but lately, such descriptions have become rare. This isn’t because the AES encryption feature has been cut back, but rather because it has become a standard feature in almost all solid-state drives, so common that it no longer needs promotion. So, what exactly does it do?
Software Encryption and Hardware Encryption #
Software encryption uses various software programs to encrypt data in logical volumes. When the hard drive is first encrypted, a unique key is generated and stored in the computer’s memory. This key is encrypted using the user’s password. When the user enters the password, the system unlocks the key and allows access to unencrypted data on the hard drive. Copies of the key are also written to the hard drive. Software encryption acts as an intermediary for applications to read/write data on the device; when data is written to the hard drive, it is encrypted with the key and then written to the disk. When data is read from the hard drive, the same key is used to decrypt the data before it is provided to the application.
Software encryption is cost-effective but its security is only as strong as the device it is used on. If hackers crack the code or password, the encrypted data becomes exposed. Furthermore, because encryption and decryption are performed by the processor, the overall system speed can slow down. Software encryption has another weakness: after system startup, the encryption key is stored in the computer’s memory, making it vulnerable to low-level attacks.
Self-encrypting drives (SED) use hardware encryption, which takes a more holistic approach to encrypting user data. SEDs are equipped with built-in AES encryption chips that encrypt data before it is written to NAND flash memory and decrypt it before reading from NAND media. Hardware encryption is positioned between the operating system installed on the hard drive and the system BIOS. When the hard drive is first encrypted, the encryption key is generated and stored in NAND flash memory. When the system is first started, a custom BIOS loads and requests the user’s password. After entering the password, the contents of the hard drive are decrypted, granting access to the operating system and user data.
Self-encrypting drives also use a built-in encryption chip to dynamically encrypt/decrypt data, responsible for encrypting data before writing to NAND flash memory and decrypting data before reading it. The host CPU is not involved in this encryption process, reducing performance losses associated with software encryption. In most cases, when the system is started, the encryption key is stored in the solid-state drive’s onboard memory, making it more difficult to retrieve and less susceptible to low-level attacks. This hardware encryption method is invisible to the user and provides a high level of data security. Hardware encryption cannot be disabled and does not impact performance.
What is AES Encryption? #
AES stands for Advanced Encryption Standard, and solid-state drives use AES encryption to protect the data stored within them. AES encryption can have a key length of up to 256 bits.
The encryption and decryption of AES are performed by the hardware controller of the solid-state drive, without any loss in performance. The data stored in the flash memory chips is all encrypted.
By setting a hard drive password in the BIOS settings, you can protect the data on the hard drive. When starting up the computer, you must first enter the correct password to access and read/write the files on the drive. Once the correct password is entered to unlock it, subsequent usage is transparent, and the software does not perceive the encryption’s presence.
Limitations of AES Encryption and Unexpected Uses #
AES encryption, despite its robust security, can only protect data when the computer is powered off. The process of booting up and running the operating system after entering the password is not encrypted.
Even if a user password is not set, the AES encryption engine still functions normally, and the data stored in the solid-state drive’s flash memory remains encrypted. However, it does not serve the purpose of preventing unauthorized access. Instead, it unintentionally accomplishes a crucial effect: data randomization.

Computers use binary to represent data, and the data stored on a hard drive may consist of continuous sequences of 0s or 1s. This is not a problem for mechanical hard drives, but solid-state drives use flash memory as their storage medium, which is sensitive to continuous sequences of 0s or 1s. For a flash memory cell, the electric potential states stored in the “neighbor” cells in the surrounding areas can affect the threshold voltage of the central cell.
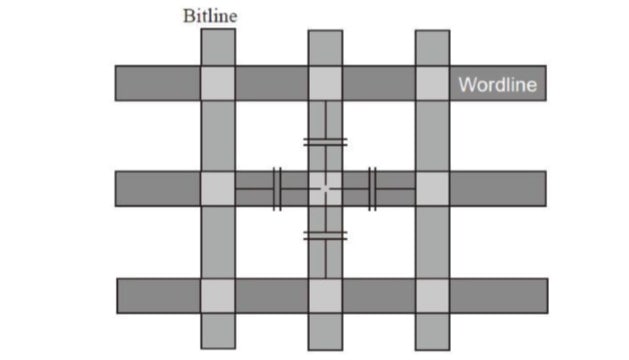
Continuous sequences of all 0s or all 1s being written can easily lead to an imbalance of electric charge within the flash memory, causing interference and reducing data reliability. Encrypted ciphertext, on the other hand, appears very chaotic and unreadable, resembling gibberish. This characteristic aligns with the need for data randomization in flash memory storage, preventing continuous sequences of 0s and 1s.

AES encryption inadvertently assists solid-state drives in achieving data randomization, ensuring a well-distributed distribution of 0s and 1s, reducing interference between adjacent memory cells. This can be seen as a valuable byproduct of AES encryption in solid-state drives.
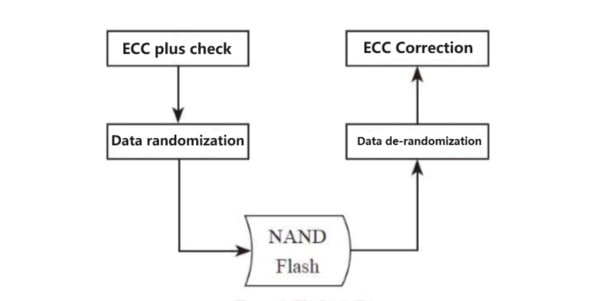
It is precisely because of these valuable features of AES encryption that it has become a standard feature in almost every solid-state drive. It has gradually become as ubiquitous as the SATA interface. While the demand for hard drive encryption among home computer users is relatively low, many people have gradually forgotten the important role that AES encryption plays in SSDs.
A great solid-state drive, like AES encryption, quietly and reliably performs its work, allowing users to completely forget its presence and enjoy the smooth computing experience it provides.







