On May 25th, Kaspersky released a security blog post, stating that variants of the ShrinkLocker ransomware have been found in Mexico, Indonesia, and Jordan. Currently, it targets only commercial PCs in organizations and manufacturing sectors, using BitLocker for encryption extortion.

ShrinkLocker is notable for using VBScript (an old Windows programming script deprecated starting with Windows 11 24H2) to identify the specific Windows operating system used by the host PC.
The malicious script runs OS-specific BitLocker settings and activates BitLocker on PCs running Vista, Windows Server 2008, or newer versions. If the operating system is too old, ShrinkLocker automatically deletes itself without leaving any traces.
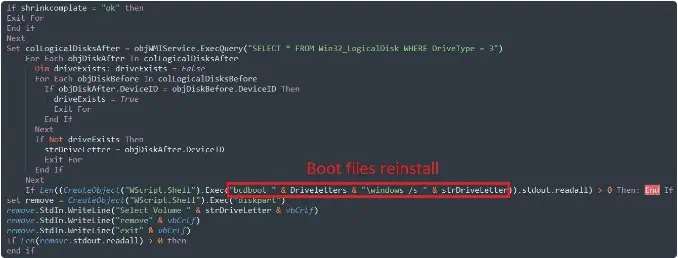
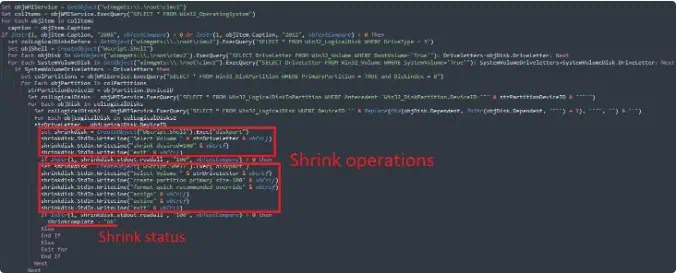
ShrinkLocker reduces all hard drive partitions by 100MB and uses the stolen space to create a new boot partition named “Shrink”Locker.
ShrinkLocker also removes all protectors used to safeguard encryption keys, making it impossible for victims to recover them later. The script generates a 64-character random encryption key, sends it and other information about the computer to the attacker, deletes logs storing ShrinkLocker activity, and finally forces the computer to shut down, fully locking and encrypting all disks using the newly created boot partition.
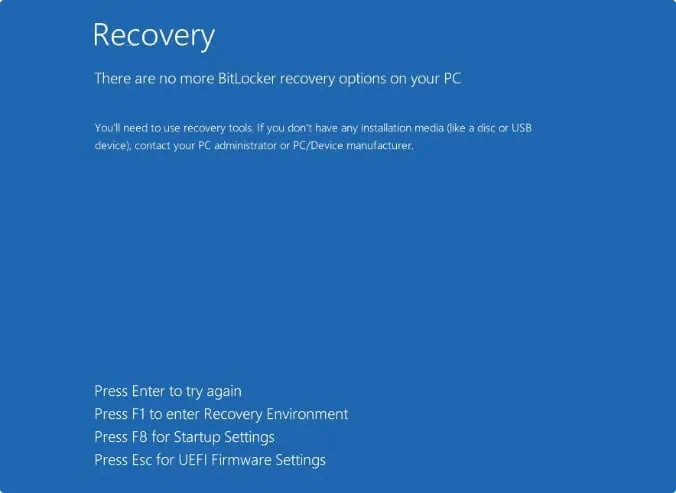
Once a device is infected with ShrinkLocker ransomware, the hard drive often becomes “bricked.” Kaspersky believes the creators of ShrinkLocker must have “extensive knowledge” of various obscure Windows internals and utilities to execute such a nearly traceless attack.
Kaspersky’s experts have not been able to identify any method to trace the attack source or the information transmission source. However, they did find the ShrinkLocker script on a single hard drive of an affected PC that had not configured BitLocker.

Disclaimer: This article is created by the original author. The content of the article represents their personal opinions. Our reposting is for sharing and discussion purposes only and does not imply our endorsement or agreement. If you have any objections, please contact us through the provided channels.



