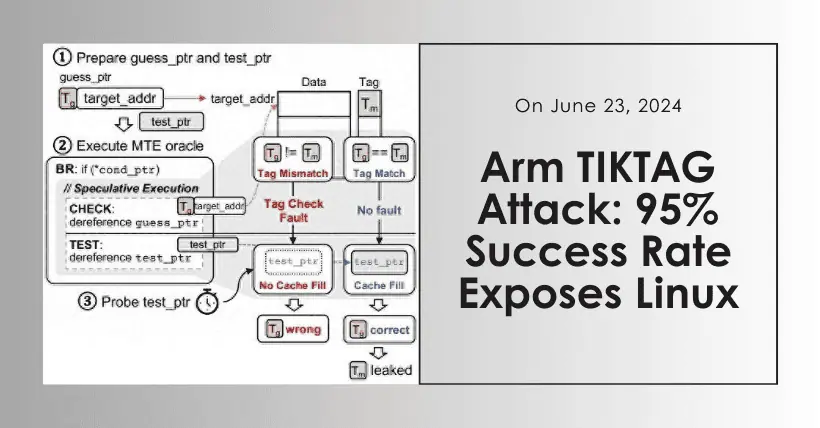
Recently, a South Korean security research team has unveiled a new speculative execution attack technique named TIKTAG, targeting ARM’s Memory Tagging Extension (MTE). This technique can bypass critical protection mechanisms against memory corruption with a success rate of over 95%.
MTE is a feature added in the ARM v8.5-A architecture (and subsequent versions) primarily for detecting and preventing memory corruption. The system uses a low-overhead tagging technique, allocating 4 bits to tag 16-byte memory blocks (1 byte = 8 bits). This mechanism helps ensure that the pointer tags match the tags of the memory region being accessed, thereby reducing unauthorized memory access and abuse.
Editor’s note: MTE is categorized into synchronous, asynchronous, and asymmetric types, each balancing security and performance. However, the TIKTAG vulnerability indicates that even the most well-designed and high-level protection can have flaws.
Researchers observed two highly efficient and fast programs, TIKTAG-v1 and TIKTAG-v2, targeting speculative execution to leak MTE memory tags.
TIKTAG-v1
The functions used in TIKTAG-v1 include speculative contraction in branch prediction and CPU data prefetching.
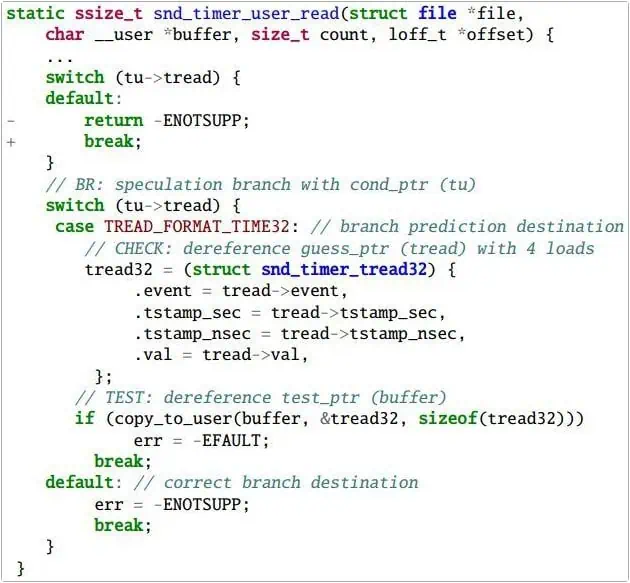
Researchers found this tool particularly effective in attacking the Linux kernel by exploiting speculative memory access, though it requires some manipulation of kernel pointers. Malicious code alters the kernel pointers and uses system call functions to access and speculate the cache state to obtain memory tags.
TIKTAG-v2
TIKTAG-v2 primarily focuses on store-to-load forwarding in processor timing speculation.
The first step involves storing a value to a memory address while simultaneously loading from the same address. The value is passed to the next tag, successfully loading and changing the shared cache state.
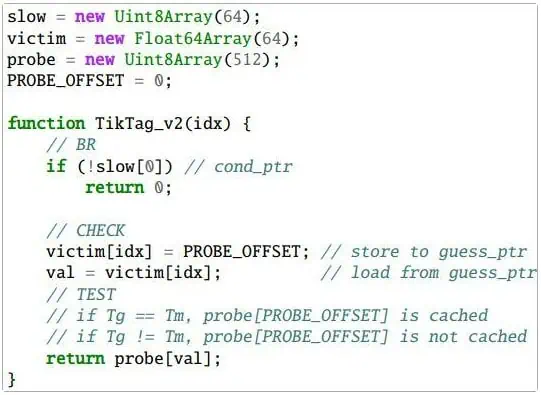
On the other hand, a mismatch prevents forwarding, and the cache state remains unchanged. If the attacker checks the cache state after speculative execution, they can infer the tag check results.
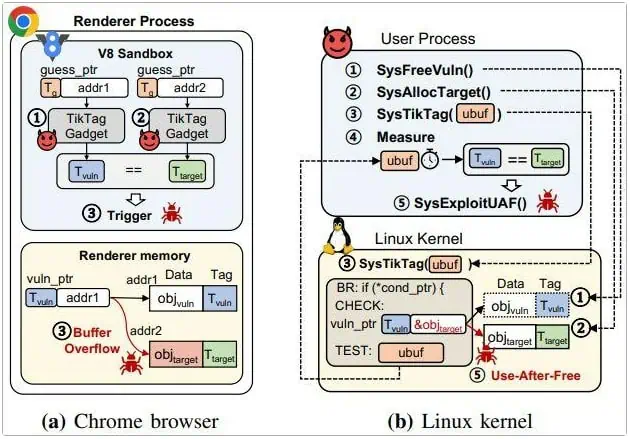
It turns out that TIKTAG-v2 is effective against target vulnerable processes such as the Google Chrome browser, specifically focusing on parts including the V8 JavaScript engine.
Response
ARM stated in an announcement that the TIKTAG attack is very powerful but noted that using speculative methods to disclose allocation tags at the architecture level remains secure. They emphasized in the announcement that allocation tags are not hidden in the address space.
ARM wrote in the announcement: “Since Allocation Tags are not a secret to software in the address space, the speculative mechanism revealing the correct tag values is not considered a breach of architectural principles.”
The Google Chrome security team acknowledged these issues but chose not to fix them, noting that the V8 sandbox does not keep memory data and MTE tags secret. Additionally, the Chrome browser has not yet enabled MTE-based defenses, so fixing these vulnerabilities is not urgent.

Disclaimer: This article is created by the original author. The content of the article represents their personal opinions. Our reposting is for sharing and discussion purposes only and does not imply our endorsement or agreement. If you have any objections, please get in touch with us through the provided channels.